compromise assessment malaysia
Compromise assessments CA answer the fundamental cyber security question Are we breached. Why has Bank Negara Malaysia BNM mandated Large Financial Institutions to perform Compromise Assessment.

Facts Of Ransomware Attacks 2021 Malaysia Lgms News
It takes organizations an average of 191 days to identify a data breach.

. Increasingly companies around the world understand that Compromise Assessments are a basic business. A body corporate which commits an offence under the Competition Act will attract a fine of up to Malaysian Ringgit RM 5 million while a second or subsequent offence will result in the. What is Compromise Assessment.
On particular example was a large financial institution in Southeast Asia that was required to conduct a Compromise Assessment on all corporate of endpoints in a very short timeframe. The Role of Compromise Assessments in Enterprise Security. Our approach to Compromise Assessment The most sophisticated threat actors dedicate their time to finding ways of evading detection from traditional defence mechanisms such as.
Is Your IT Infrastructure Secured. Malaysia through operations of branches and subsidiaries. How to Get a Penetration Test in Malaysia Build a Risk-Free System with Pen Testing Multiple cybersecurity studies have reported an exponential rise in digital threats in Malaysia.
While penetration tests focus on finding vulnerabilities a compromise assessment focuses on whether an organization was breached without knowing it he explains. Our Compromise Assessments are an essential business need for all organisations. In addition a compromise assessment can help highlight the risk associated with a compromise not being effectively communicated to seniorexecutive leadership within your.
Using Deloittes Cyber Compromise Assessment CCA on your estate will help identify if there is a current or indicators of a past compromise of your network - utilising the latest threat. Compromise Assessment is an advanced threat diagnostic ATD that detects the clear and present cyber dangers that already exists in your organization. Usually there are a few reasons companies do a Compromise Assessment.
It will investigate your. Bank Negara of Malaysias Risk Management in Technology. Bank Negara Malaysia now encourages financial institutions to conduct a Compromise Assessment CA through a.
Our CA service delivers a high-level review and audit of your organizations IT. A compromise assessment is an objective survey of a network and its devices to detect unknown security. 1 To comply with local laws regulations Eg.
The compromised or not state of your environment your ability to identify vulnerabilities your. Material technology projects refers to projects which involve critical systems the delivery of essential services to customers or. In this upcoming webinar CEO.
Compromise Assessment Firmus 2020-06-14T1449110800. Compromise Assessment Malaysia LGMS 1 Cyber Security Provider 7 Who trust LGMS for professional cybersecurity services. Performing a compromise assessment gives you confidence in your awareness of.
Diversity Free Full Text Can Thailand Protect 30 Of Its Land Area For Biodiversity And Will This Be Enough Html
Lgms Ipo 8 Key Things Investors Should Know

Facts Of Ransomware Attacks 2021 Malaysia Lgms News

Ransomware Attacks In 2022 Malaysia S Ultimate Guide

Ransomware Attacks In 2022 Malaysia S Ultimate Guide
Ransomware Attacks In 2022 Malaysia S Ultimate Guide
Pdf A Case Study Of Unemployment Among Graduates In The Klang Valley

Facts Of Ransomware Attacks 2021 Malaysia Lgms News
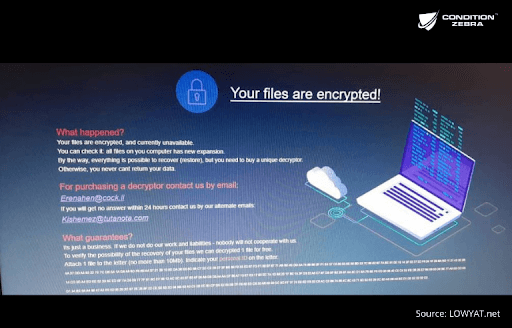
Ransomware Attacks In 2022 Malaysia S Ultimate Guide
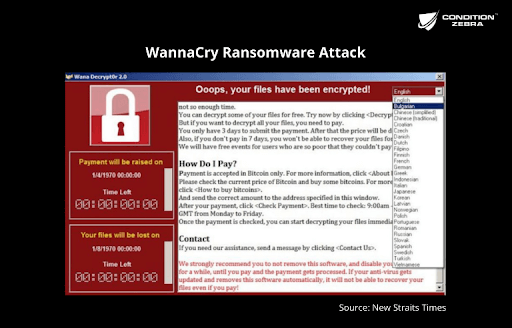
Ransomware Attacks In 2022 Malaysia S Ultimate Guide
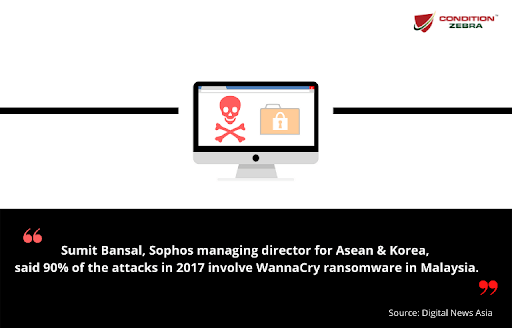
Ransomware Attacks In 2022 Malaysia S Ultimate Guide

Pdf Developing A Framework Of Internationalisation For Higher Education Institutions In Malaysia A Swot Analysis

Teamtnt Upgrades Arsenal Refines Focus On Kubernetes And Gpu Environments
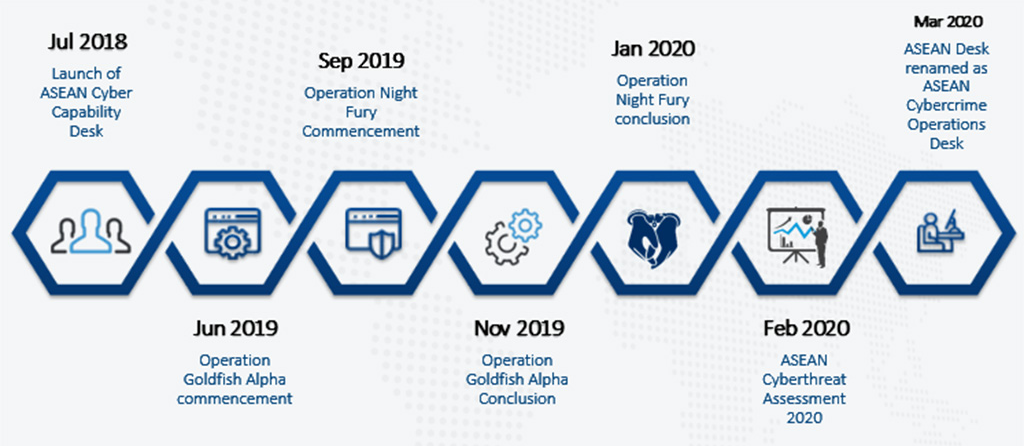
Asean Cybercrime Operations Desk

Pdf Visitation Rights Under Family Law Do Children Have A Right Of Refusal
Pdf Road Traffic Accident In Malaysia Trends Selected Underlying Determinants And Status Intervention
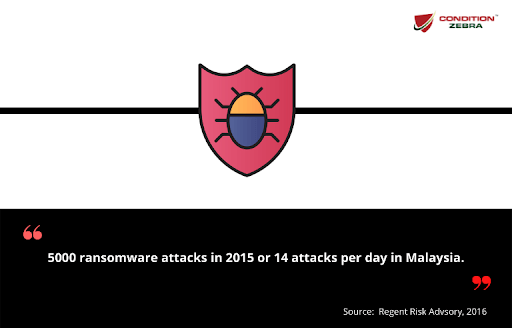
Ransomware Attacks In 2022 Malaysia S Ultimate Guide

Vulnerability Assessment Malaysia Delivering Cyber Security Value

Red Flags How To Spot A Business Email Compromise Scam Wiadomosci Bezpieczenstwa
Comments
Post a Comment